Virtual Private Network (VPN)
Learn how VPN works on the Digibee Integration Platform and how you can use it.
How VPN works
IPSEC, the protocol used in Digibee's VPN, creates secure internet connections in two phases:
Phase 1: Establishing a secure channel
In Phase 1, a secure tunnel is created for information to pass between two VPN gateway devices. During this step, the devices exchange credentials to verify each other's identity and agree on the security settings.
Phase 2: Securing data transmission
After Phase 1 is done, the devices move to Phase 2. In this step, they establish encryption and authentication rules to protect the data transmitted between them.
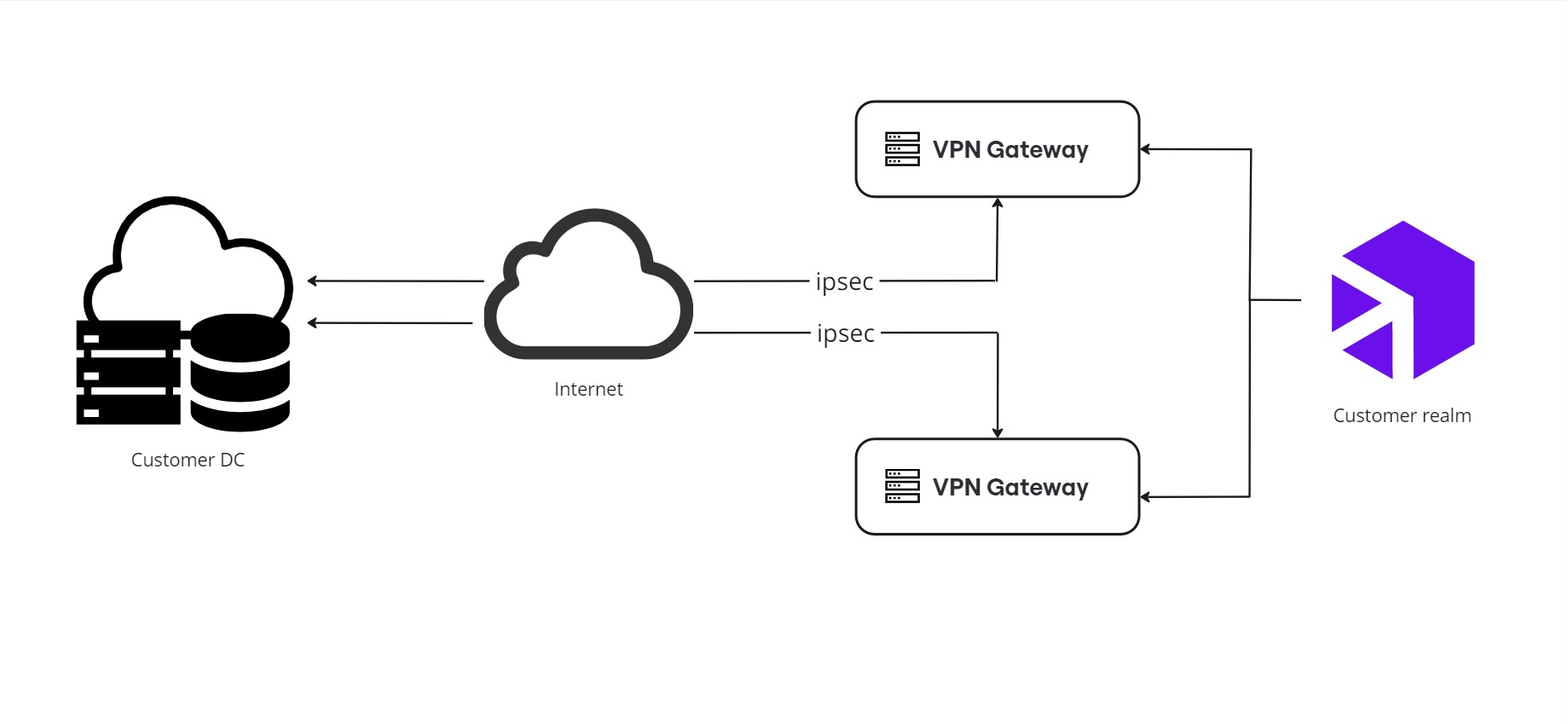
The size of the VPN gateway is based on the number of RTUs in your subscription. For more details, check our documentation on Capacity and Quotas.
How to use VPN
Limitations
In our Platform, the VPN has some known limitations:
Our current VPN setup doesn't support redundancy. If you need redundancy, we suggest using ZTNA.
The FTP connector doesn’t work with VPN/NAT connections.
You can't connect to subnets that overlap with Digibee’s internal network.
Digibee SaaS subnet (Brazil): 10.158.0.0/20 (default) and 10.0.0.0/14 (range: 10.0.0.1 to 10.3.255.254)
Digibee SaaS subnet (USA): 192.168.0.0/24, 172.19.0.0/16 (range: 172.19.0.1 to 172.19.255.254) and 172.12.0.0/16 (range: 172.12.0.1 to 172.12.255.254)
The peer used to connect in Phase 1 must be a /32 subnet.
Last updated
Was this helpful?