OAuth2 for secure API access
Protecting sensitive data and building customer trust starts with securing your APIs. OAuth2 ensures secure API access, offering a solution to modern security challenges, and makes this easier by using tokens to keep data safe and reduce security risks.
This Use Case in Action highlights how OAuth2 addresses common security challenges, such as unauthorized access, data breaches, and inefficient access control. Through practical implementation on the Digibee Integration Platform, we’ll show how tokenized authentication and role-based scopes enable secure, scalable API interactions.
OAuth and OAuth2 framework
OAuth is an open standard for access delegation, allowing secure API interactions without sharing user credentials. OAuth2, its successor, simplifies this process with token-based authentication and role-based scopes, making it more suitable for dynamic, multi-user applications. The token-based approach eliminates the need to expose sensitive credentials while allowing fine-grained access control through scopes, making it ideal for dynamic, multi-user applications.
On Digibee, OAuth2 can be implemented through pre-configured providers, custom OAuth providers, or external systems. Unlike OAuth2, OAuth requires cryptographic signatures for each API call, offering a more complex but secure flow for legacy integrations.
Challenges addressed
APIs manage operations like authentication and secure access to resources. Without adequate access controls, they may present risks of data breaches, inefficiencies, and scalability issues. Sensitive data may be exposed due to weak restrictions, manual permission management can lead to errors, and static security models often fail to support growing user bases. Additionally, insufficient role-based permissions can result in overexposure of critical information, further compromising security.
OAuth2 addresses these challenges with:
Role-based scopes: Tailoring permissions to user roles. For example:
Salesperson: Access to profile data (such as name, email, age).
Manager: Access to profile and address data.
Admin: Access to all claims, including financial data.
Tokenized authentication: Eliminating static credentials for enhanced security.
Dynamic claims filtering: Enforcing access rules dynamically to align with policies.
Key concepts
Scopes: Define the permissions tied to each role, determining what data a user can access. For example:
Viewer: Access only to read basic information, such as names and emails.
Editor: Access to read and modify profile details.
Admin: Full access to all data, including sensitive financial or operational details.
Claims: Provide additional metadata to customize permissions for API interactions.
Token-based authentication: Replaces sensitive credentials with secure tokens for enhanced protection.
Credential provider: Validates credentials and issues tokens.
Putting theory into practice
Consider an API exposing customer data (for example, profile, address, banking information) protected only by an API key. This approach lacks the granularity needed to segregate access by role, risking overexposure of sensitive information. OAuth2 provides a tokenized approach, ensuring secure access through credential validation, token generation, and claim management.
This Use Case focuses on the Token Generator pipeline, which interacts with a Credential Provider to validate incoming credentials, request tokens, and filter claims based on defined scopes. The implementation ensures flexible integration with OAuth2, supporting both pre-configured providers available on Digibee, and external OAuth providers.
The diagram below illustrates the overall flow, from credential submission to API access, demonstrating how the Token Generator pipeline secures API interactions:
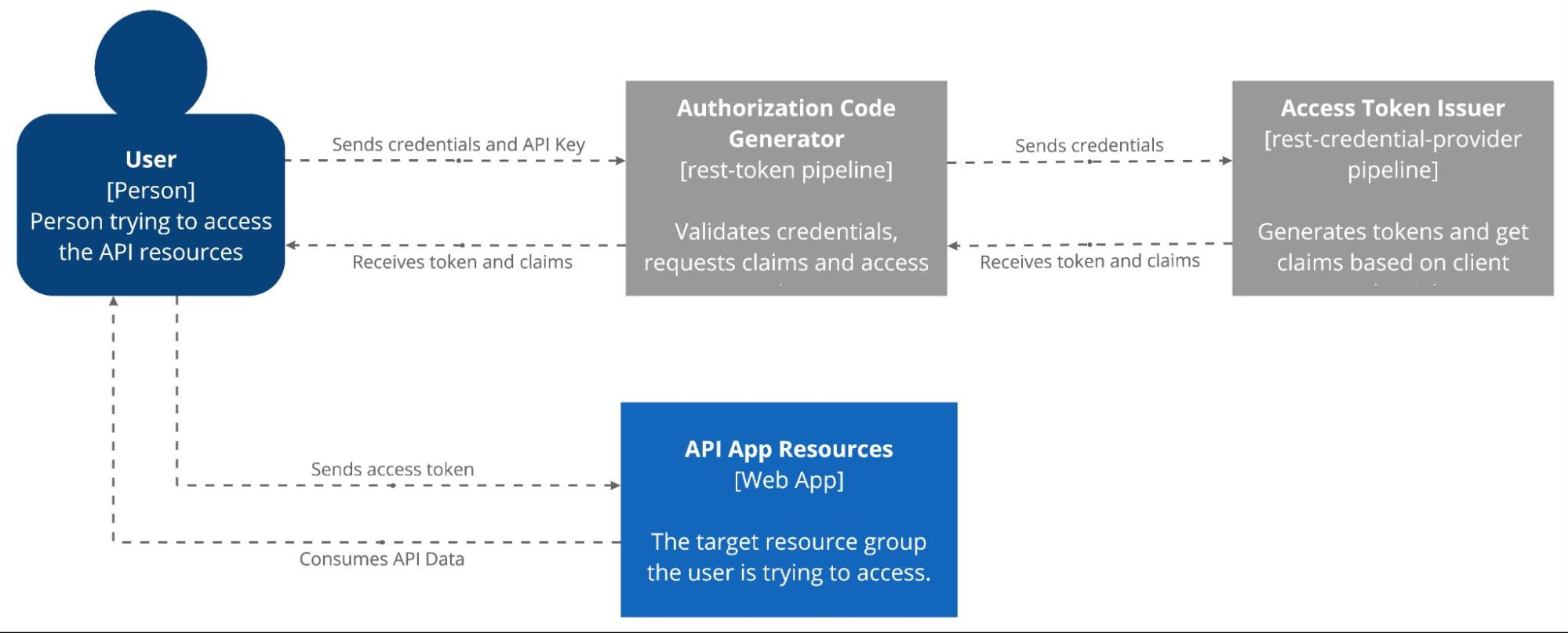
How the proposed solution works
This Use Case focuses on the Token Generator pipeline to demonstrate OAuth2 in action. Here's how it works:
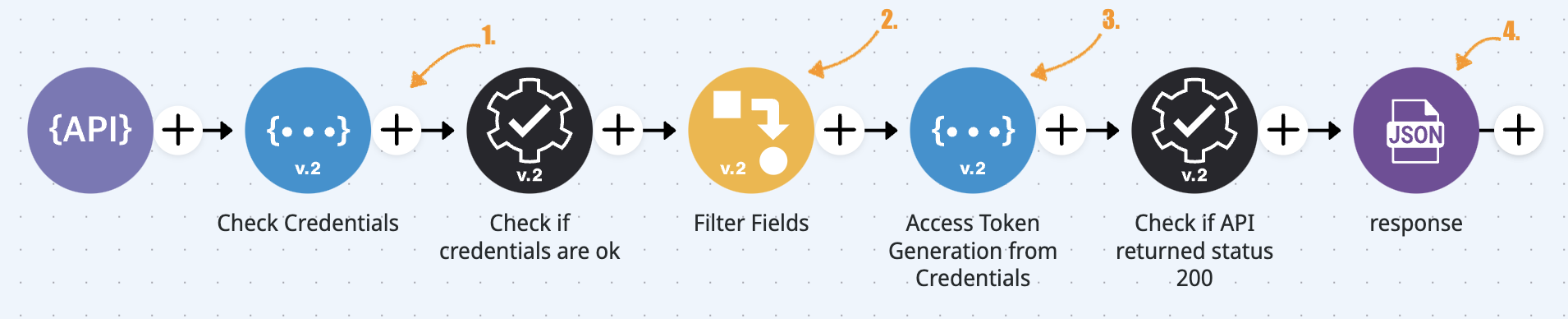
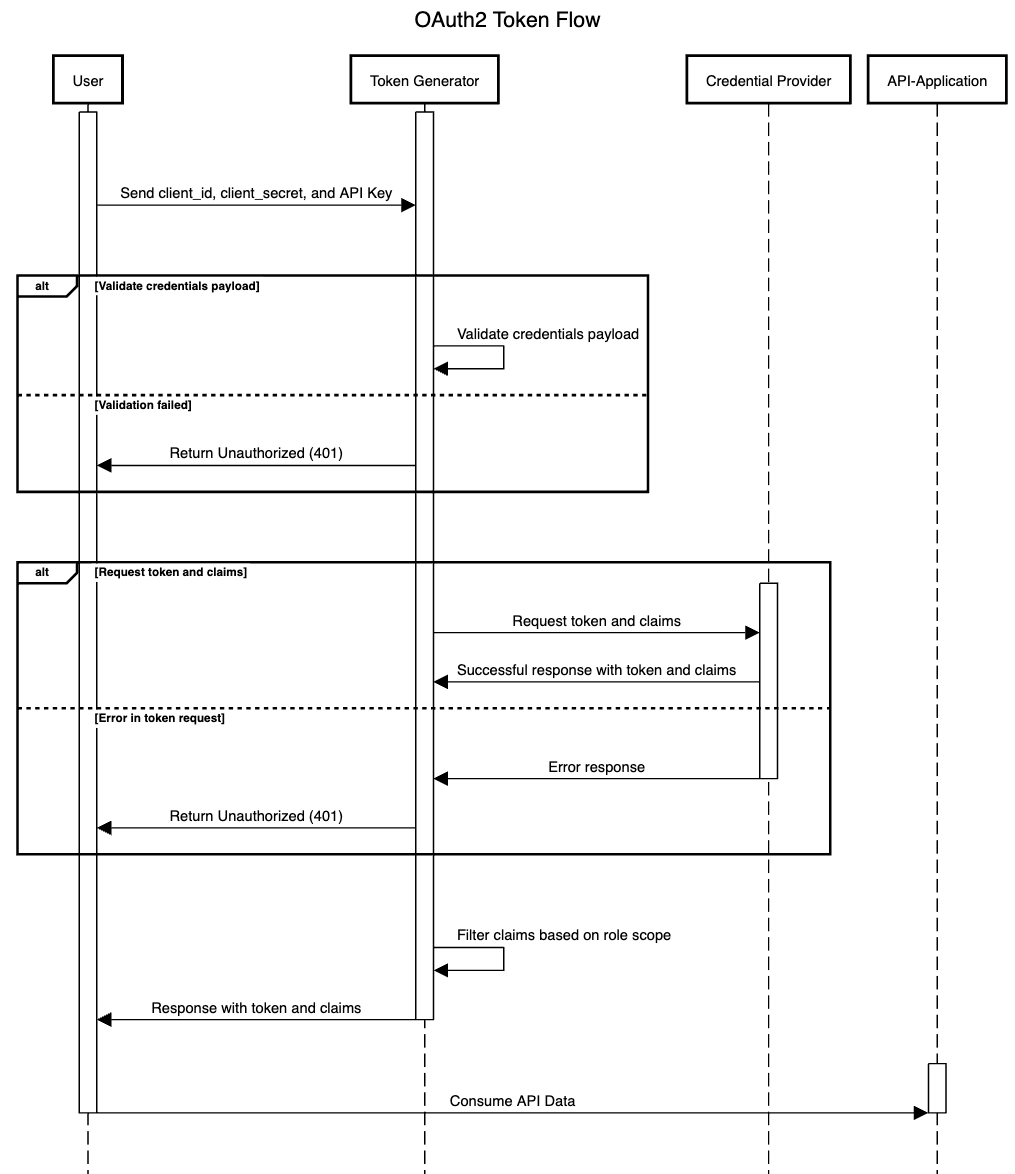
Credentials validation: The user submits
client_id,client_secret, and API Key. An Assert connector checks the payload, throwing a401 Unauthorizedif validation fails.Claims filtering: Claims are categorized (for example,
profile_claims,address_claims,banking_claims) and filtered by scope using a JOLT Transformer or similar transformer connector, ensuring access matches the user's role.Token request: Valid credentials are sent to the Credential Provider pipeline using a REST connector. A status
200response is validated, while errors trigger an exception.Response: Filtered claims are restructured and packaged with an
access_token, scope, and other metadata for secure API access.
Benefits of OAuth2 for secure API access
Integration flexibility: Supports native and custom OAuth configurations, enabling secure integration with a variety of systems.
Enhanced security: Implements role-based permissions and tokenization to protect sensitive data.
Operational efficiency: Streamlines access control for scalable integrations.
Scalability: Adapts to growing user bases with dynamic configurations.
Compliance: Aligns with modern data protection standards.
Final thoughts
OAuth2 redefines API security, providing granular access control and operational efficiency. Digibee enhances this capability with native and custom OAuth provider support, ensuring flexibility for diverse use cases.
To solidify your understanding, take this Enhancement in Security with OAuth2 challenge in Digibee Academy. For more information, visit the Documentation Portal or explore our Blog for additional insights.
If you have feedback on this Use Case or suggestions for future articles, we’d love to hear from you through our feedback form.
Last updated
Was this helpful?