OAuth2 integration model with Digibee
Learn how to implement an OAuth2-based integration model to securely and efficiently authenticate and authorize connections.
Architecture
Overview
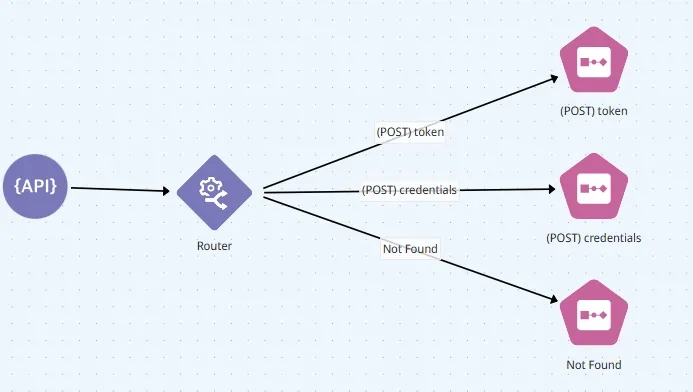
Description
Detailed flow
Payloads
1. Credential generation
2. Token retrieval
3. Token refresh
4. Credential removal
PreviousNotification model in event-driven integrationsNextUsing JSONPath to validate numbers with specific initial digits
Was this helpful?